Server Hardening: Securing SSH Access with Enhanced Protection
Server Hardening: Securing SSH Access with Enhanced Protection
The internet is a hostile environment. If you have a private server with SSH access, it’s essential to apply security measures to prevent unauthorized access.
Check for Malicious Access Attempts
You can see authentication attempts to your server using:
sudo grep sshd /var/log/auth.log
You’ll likely find several brute-force attempts from automated bots or scripts.
Steps to Secure Your Server (Hardening)
✅ 1. Create a New Non-Root User
Replace USERNAME with your preferred username:
adduser USERNAME
usermod -aG sudo USERNAME
su - USERNAME
sudo whoami
🚫 2. Disable Root Login
Edit the /etc/ssh/sshd_config file:
...
PermitRootLogin no
...
Then restart the SSH service:
sudo service ssh restart
🔁 3. Change the Default SSH Port
Port 22 is the default and often scanned. Choose a high port between 49152–65535, for example:
...
Port 65222
...
Update the /etc/ssh/sshd_config and restart SSH.
🔒 4. Restrict Allowed Users
Only allow the new user you created:
...
AllowUsers USERNAME
...
⛔ 5. Limit Authentication Attempts
...
MaxAuthTries 3
...
🔥 6. Configure Firewall with UFW
sudo apt update
sudo apt install ufw
sudo ufw default allow outgoing
sudo ufw default deny incoming
sudo ufw allow 65222
sudo ufw enable
sudo ufw status
🛡️ 7. Install and Configure Fail2Ban
sudo apt install fail2ban
cd /etc/fail2ban/
sudo cp jail.conf jail.local
Edit jail.local with the following configuration:
[DEFAULT]
...
[sshd]
enabled = true
backend = systemd
port = 65222
filter = sshd
logpath = /var/log/auth.log
maxretry = 3
bantime = 6h
ignoreip = 127.0.0.1/8
▶️ 8. Enable Fail2Ban
sudo systemctl restart fail2ban
sudo systemctl enable fail2ban
sudo systemctl status fail2ban
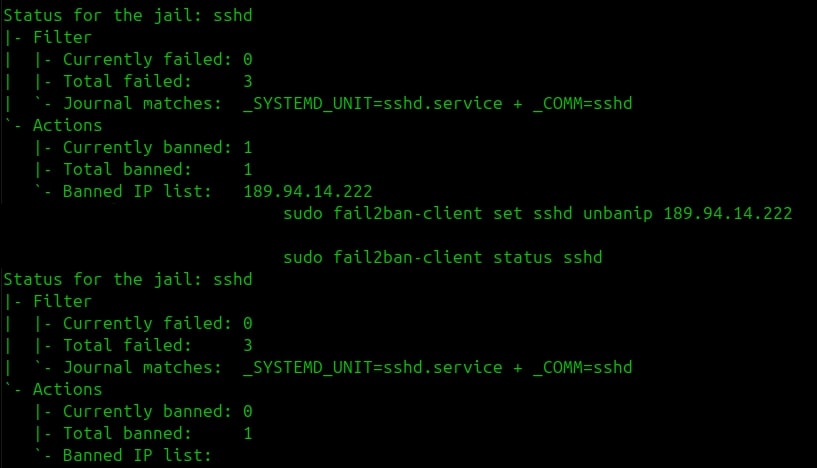
Attempt to log in 3 times with a wrong password, then check banned IPs:
sudo fail2ban-client status sshd
To unban an IP:
sudo fail2ban-client set sshd unbanip X.X.X.X
Conclusion
By following these SSH hardening practices, your server becomes more secure and less vulnerable to automated attacks.
Security starts with prevention! 🔐